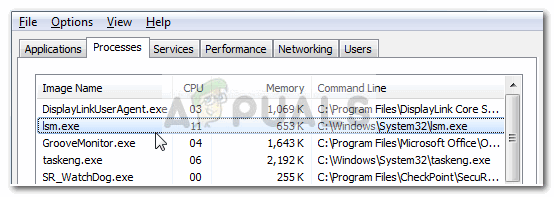
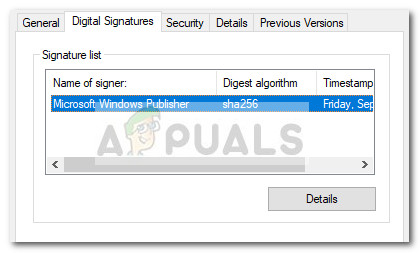
While there’s a high chance that the process is indeed legitimate, users are encouraged to do the below-specified investigations in order to confirm that they are not dealing with a virus infection.
What is lsm.exe?
The genuine lsm.exe executable is a completely legitimate and is actually a core Windows system process. Lsm comes from Local Session Manager Service. This key process is issued by default on Windows 7, Windows 8 and Windows 10. The purpose of the genuine lsm.exe process is to manage all connections related to a server that acts as a terminal on the hosted machine. Although the process is often associated with explorer crashes and performance conflicts in games, it should be regarded as a critical component. Without it, your system will be unable to dispatch interactive user sessions. It should be noted that the lsm.exe process has increased in importance starting with Windows Vista. In Windows Vista and all ulterior versions, the process is not only responsible for managing local session connections but also for managing virtualized terminal server sessions.
Potential security threat?
While the chances of dealing with a malicious executable are slim, there are at least three known virus/trojans variations that were given the same name as the lsm.exe in order to avoid getting detected by security threats:
Packed.Win32.Krap.hmWorm.Win32.VBNA.bBackdoor:Win32/Slingup.A
Note: Most of these malware variations will end up using your PC’s resources to mine for Bitcoin or other cryptocurrencies. In order to make sure that you’re not actually dealing with a virus infection, let’s investigate the executable for any malicious activity. To do this, open Task Manager (Ctrl + Shift + Esc) and locate the lsm.exe process in the Processes tab. Then, right-click on the lsm.exe process and choose Properties. In the lsm.exe Properties screen, expand the Digital Signatures tab and check whether the Name of signers corresponds to Microsoft Windows Publisher. If it does, you can rest easy as the file is definitely not malicious.
Note: A huge giveaway that will surely tell you if the process is malicious or not is the name. While the original lsm.exe has a small l (L) in the name, the fake (malicious) executable will have a capital I (i). If there’s no signer under Signature list, we’ll need to perform additional investigations. To do this, right-click on the lsm.exe process and choose Open File Location. If the revealed location is different than C:\ Windows \ System32, you’re most likely dealing with a malicious executable. You can confirm or infirm your suspicions by uploading the newly discovered executable to VirusTotal for analysis. Note: A common location for malicious executables that are posing as the legitimate Ism.exe is in C:\ Users \ Your Name \ AppData \ Roaming \ lsm.exe. If the analysis reveals suspicious activity, we highly recommend that you scan your system with a powerful malware remover like Safety Scanner or Malwarebytes. If you’re unsure of how to do this, follow our in-depth article (here) on using Malwarebytes to remove any trace of malware from your system.
Should I remove lsm.exe?
As we already established below, the lsm.exe process is commonly used for the remote configuration of different aspects associated with the terminal session. Removing the lsm.exe executable or preventing the process from functioning will most likely have devastating consequences to the stability of your system. Because of this, you should never remove the genuine lsm.exe from your system. In the event that you observe high CPU and RAM usage caused by the lsm.exe process and you’ve made sure that the process is legitimate, simply reboot your system and the usage should improve at the next startup.
What is pcdrcui.exe? How to Fix pcdruci.exe Corrupted Error on Windows?What is Msiexec.exe? Fix Msiexec.exe Access Denied Error on WindowsWhat is “msedge.exe.exe”? and How to Fix It?How to Fix High CPU and Memory Usage By csrss.exe